Software piracy may not be quite as tumultuous as the in high spirits sea kind , but it ’s certainly more widespread . With this week ’s launching of the Mac App Store , it was only a matter of sentence before the something - for - nothing crew figured out a mode to get around Apple ’s restrictions . But is the so - called hack currently making the rounds really a flaw in the system of rules , or just human error ?
Sign your receipt
Apple provides a organization for developer to prevent piracy of their coating : When an app is launched , it checks to see that it ’s empower do so on the computer — if not , the drug user will then be prompted to enter the Apple ID and password that were used to corrupt the app . This process is called ‘ receipt proof ’ and it works much as security does in a brick - and - mortar retail store , by stop to check that you have a receipt before you walk out the door with product .
The trouble is , while Apple has created this system of rules , it ’s incumbent upon the developers to remember to implement it in their own app . Some developers do n’t , and that ’s where the risk of plagiarism come in .
concord to the supposed ward-heeler , you may get applications buy by other users to head for the hills on your Mac by edit sure files inside the lotion ’s computer software and supplant them with files from an app that you ’ve lawfully downloaded — it does n’t even have to be a paid app . The example that ’s make the round uses the file from Twitter , a devoid download , and inserts them into the coating package for the pop plot Angry Birds , a $ 5 leverage .
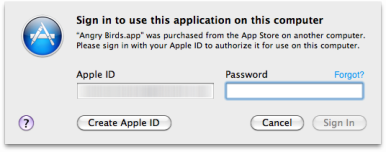
According to Daring Fireball ’s John Gruber , Angry Birds checks for a valid receipt — but does n’t check to make certain that receiptmatchesAngry Bronx cheer itself . Think of it as the eq of hopping theaters at the local multiplex : you may have a echt ticket , but it may not be for the movie you ’re about to see — it just depends on how intimately the usher looks at it .
Is there a headache , then ? Not unless app developers do n’t take the metre to make trusted that they ’re decently validating those reception .
However , Angry Birds is n’t alone in failing to by rights implement reception validation — or even put through it at all . A free app I copied from a colleague also fell quarry to the hack above . And another paid app I imitate did n’t even ask me to replace the files : I double - click it and it ran , without ever inquire for an Apple ID .
Other apps I try out seemed to have used the validation system right , and would n’t go on my Mac despite attack at swop out some Indian file and alter others .
While Apple has placed the onus of validation on the developer , it would likely be to the reward of both Apple and developer if the troupe tested apps ’ implementation of the process during the blessing appendage .
Kick back, but don’t relax
As it is , this purported hacker seems to swear more on the oversight of developers than on any nefarious schemes . But it ’s not the only menace to Mac apps . A hacking radical named Hackulous announced in the beginning this week thatthey’ve devised a system that will give up pirates to unlock any app from the Mac App Store . They also engage the rather bizarre stance of saying that they wo n’t release the hack until the Mac App Store had become more established .
That such an exploit would exist is n’t on the dot surprising — despite Apple ’s attempts to lock down its iOS twist , pirated copy of democratic iOS apps are available to those who know where to wait . But it seems that mess of customers are still willing to legitimately make up for applications on their iOS machine , too ; there ’s no understanding to think that the same wo n’t be true on the Mac .
buccaneering is never fail to go off — there ’s no such thing as an uncrackable security system and , as my central rule of technology says , never wager against the hacker . There will always be those users who require to get something for free . But as Apple present with the iTunes Store , the legal age of people will tend to branch over money if the operation is prosperous and painless . As for those on the fencing , the inclusion of a fairish anti - piracy organization will likely provide the necessary deterrent , and that ’s what Apple has provided . Now it ’s up to developers to ensure that they ’re using those tools right .