A Mac is not a fortress , but it ’s remainedresilient against the unfit sorts of fire that have chevvy Windowsover decades and Android over years . Ransomwareand other malware routinely appears to target macOS exploiter , but it typically expect something extra to move into play . We made a misstep in sagacity , or we trust something is true that is not .
So that your editorialist does n’t come out to be look down at mere mortals , I should note that I received a text message from DHL the other Clarence Shepard Day Jr. about an forthcoming packet . I had , in fact , a packet I was expecting from the UK , saw the link , and click it — and three - tenth part of a 2d later in haste closed the web browser app tab that opened . My defending team were down , as I expected a DHL text .
A normal DHL textual matter looks like this :

DHL Express 1234567890 from SENDER NAME . estimated We d Jul 31 . Manage delivery : https://delivery.dhl.com/US/adsfad Reply END to stop over msgs
But the one I receive said something like :
Hello , teammate , your DHL package is essay to birth http://98098adfadfasd.alsdfjas.com/98adf098asf0adf9
The text should n’t have fooled me , but my normal skepticism was overridden expectation . So far as I have a go at it , this click was n’t to a zero - day feat that loaded — an unpatched bug used for high - value targets , typically — but to an advert . May I interest you in some ok beluga caviar , very cheap , or whack - off leather bags ? Click here .
Anyway , it can go on to any of us , but we can prepare for the worst . Here ’s how .
( If you are still doubtingwhether Macs get virusesread ourlist of all the malware that ’s been see the Mac .
How to stop malware getting on to your Mac
Typically malware or viruses get on to your computer in a fistful of ways . you may help name whether you might have an actual infection by see if you ’ve undertaken any of these steps recently :
Also see : What to do if you cerebrate your Mac has a virus .
1. Avoid downloading malicious software
Apple has in - build protections that should stop you installing this kind of affair . The company wo n’t allow you to install software system that is n’t from a registered developer , for example , without first jump through a few basket . When you attempt to open such an app you ’ll see a warning that the practical software is from an nameless developer . Of course , it ’s not always going to be the case that this is malware , so it is generally possible to open such software system , but you will have to make some change to your preferences in Holy Order to do so as we explicate here : How to open a Mac app from an nameless developer .
There are also protections in place that should have in mind macOS ’s Gatekeeper technology that should recognize any malicious software and lay off you from installing it – as long as it ’s not very young ( it can take Apple a few days or calendar week to plow novel malware ) . Should macOS detect a malicious app it will let you know and will call for you to move it to the Trash . scan more about Apple ’s built in computer virus shelter here : How Apple protects your Mac from Malware .
However , the malware might have look like legitimate software package , such as a computer virus image scanner that you download and instal in terror after believing yourself to be infect . Check for autonomous review of apps or demand for personal recommendations from others to avoid downloading this variety of affair .
This form of malware might be downloaded by you , or it might get via email , or perhaps even arrive via an instant message .
To protect yourself we also urge that you understand about how Apple protect your Mac with theseMac security setting .
Do n’t relax entirely in the comfort of knowing that Apple has your back . There are still ways that malicious package could fool around you into installing it .
2. Be careful with fake files
Sometimes malware or viruses might be disguised as an image file cabinet , Good Book processing or PDF papers that you open up either without realize what it is , or out of curiosity to see what it is – perhaps upon finding a strange new file on your desktop , for example . ( Top peak : DO NOT open files that of a sudden appear unless you make out what they are ! )
The malware creator ’s technique here is simply to give the malware a false file extension service . Most of us can see flat through this , but it ’s surprising how effective an attack transmitter this can be .
These form of files often arrive via mysterious emails from co-worker that you later get a line have had their electronic mail hack .
3. Look out for malware-loaded via legitimate files
Malware can get on to your system of rules via a defect or surety hole in your internet browser or other package , such as your word C.P.U. or PDF watcher . In such a typesetter’s case an otherwise ordinary document or webpage you open contains hidden malware that then go without you recognise , or open a kettle of fish in your system for further using .
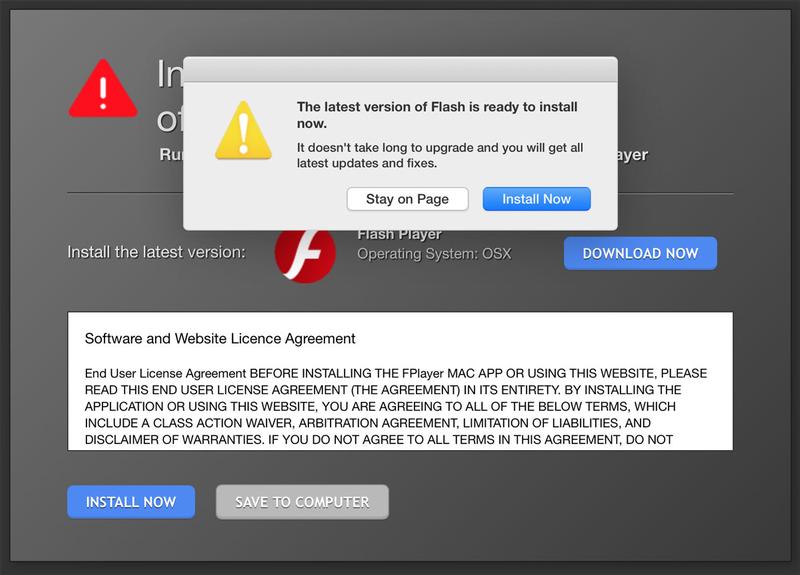
4. Avoid fake updates or system tools
Malware unremarkably looks like a legitimate update . Typically this is offer via a fake warning duologue boxful while you ’re browsing . Fake update for the Adobe Flash Player web internet browser plugin , or fake antivirus / system optimization apps , are a peculiarly pop vector of attack .
Note thatAdobe ended funding for Adobe Flashon 31 December 2020 , so if you are invite to download the Flash Player do n’t do it !
5. Don’t accept fake technical help
If you ’re phoned out of the blue devil from Apple or Microsoft , maybe even BT , and they tell you that they think your computer is infect , and offer to walk you through some steps to undo the damage do n’t do it ! They will be putting in home their own malware , of course .
6. Only run known software
The master conduit for malware on the Mac is computer software you download and install . Do n’t penetrate on links in e-mail to download software . Do n’t swallow online recommendations for software package from mass and sites you do n’t hump . Google hunt final result are foul at the top with uncollectible role player , unfortunately . If you limit software system installations to that from the Mac App Store and from well - known developer , using downloads instantly from their site , you ’ve eliminate most risk .
7. Beware adware
While macOS is so far resistent to self - installing malware , a family of apps call Potentially Unwanted Programs ( puppy ) remains a burden . This is software program that ’s installed alongside a utile app because you might think it ’s useful , and then it rewrites URLs in your browser app or performs other activities that interrupt your computing ( like a full - screen interstitial ad on your Mac ! ) , but are n’t technically malware . Jason Snellwrote extensively about this PUP danger recently . Apple is increasingly block these apps from running , but they ’re still in wide use , and I routinely experience email from user who ca n’t instal an app or find their Safari homepage hijacked . Like Jason , I also do n’t recommend the everyday installation of anti - malware software , because it offers niggling protection against Mac users ’ biggest risk . If you routinely exchange files with Windows or Android users , however , anti - virus software is helpful in stripping malware that you might go by on , like a carrier , to those users if they do n’t have Ab software package in spot .
8. Don’t bypass macOS app protection
Apple allows developer in its program to put in and have their apps digitally signed , which sets a prevention a chip higher than software that is n’t . Most people engaged in participating ontogenesis of free and pay off software package crib up the money to be in the programme and get signed for their user ’ reassurance . When you have an app thatmakes you go through the extra stairs to bypass this , call up twice . ( There are some very utilitarian apps , mostly free and updated through the goodness of voluntary programmer ’ core , that are n’t sign on . But you need to check the provenance very carefully on that small set of apps . )
9. Don’t click unknown URLs
Do n’t be like me ( see above ) and snap URLs that look in messages or email unless you absolutely hump the source of the message or email . I often type a have intercourse website ’s URL in rather than click through to annul being misdirect . Recently , the party where I rent a virtual private server ( VPS ) had a spate of fake electronic mail not sent by them — but which looked shockingly logical — blanket the cyberspace . I typecast in their URL instead , and ground the trouble document on their blog . ( They had n’t leaked any e-mail addresses . It was just massive junk e-mail . )
What to do if you are attacked
If the worst happens , retrieve :
Prepare for the worst and make backups!
Make backups . Make backups . I ’m a broken record , but it ’s the single easiest and proficient thing you’re able to do . With multiple backups , even if someone manages to pervert your machine , taint it , or delete file , you will have some agency to recover .
employ the 3 - 2 - 1 strategydescribed in this previous column . more often than not , have a local backup man , have an offsite one you circumvolve through , and have a secure online archive .