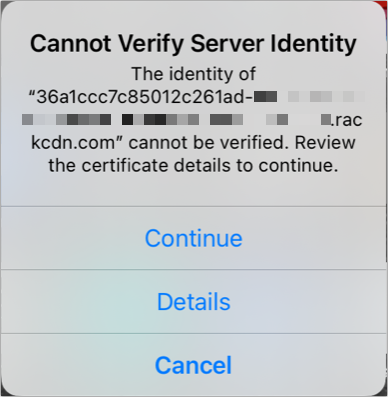
It ’s always disturb to see a warning that implies something malicious is happening . That ’s the character with an alert that can come along when an app or the operating system “ Can not Verify Server Identity ” in iOS or iPadOS or “ ca n’t verify the identity of the host ” in macOS .
This message ’s purport is to control that no unafraid connection made via a web web browser , email client , or other package has been subverted by a gentleman’s gentleman - in - the - middle ( MitM ) attack . In such a situation , an aggressor tries to fool you into accepting a different digital certificate to link than the one that ’s associated with the web waiter ’s host and knowledge base name that your machine wants to arrive at .
Third company — foretell security authorities ( CAs)—cryptographically sign the digital certificates , identity documents that server furnish when a browser app or other software client make a unattackable connection . The CAs also have signature that operating systems and web web browser build up into their release interlingual rendition . When an app essay to make a unassailable connection , it retrieve a server ’s digital certificate and validates that the certificate has a lawful signature tune from a CA by control it against its local storehouse . ( These CA counter - signature are connect to knock-down cryptographic algorithms and an attacker ca n’t falsify them without induce an error . )
It ’s quite rare in practice to find this kind of attack for the last several years because operating system and web browser have become quite outspoken about monition of a trouble or even making it hard to project out how to get around it .
With Apple ’s warning , you have the option to clack Continue and empower a link using the wrong certification . You should never agree to this unless you recognise precisely why it happened.(The only time it puddle sense is for a labor hosted on a local web or be given by an organization you know that does n’t obtain a third - party formalize certificate . Even then , you would be given a profile to set up a “ self - bless ” certification before you make a joining that prompted a warning . )
Where you typically see this egress is when connecting to a Wi - Fi hot spot before you ’ve authenticated through a portal page . Until you ’ve click an Accept button , paid for service , or lumber in , you may only make the portal pageboy — the rest of the internet is cut off .
As a result , if any apps on your iPhone , iPad , or Mac endeavour to link to a secure situation , the connection yield the certificate for its local hotspot portal server . Hence , you get an error , as that certification is n’t the right one .
To get around the problem , rap or clickCancelon any message that appears . Then either log into the hotspot net if that ’s an option or disconnect from it . you’re able to use Control Center in iOS , iPadOS , or macOS to temporarily disenable Wi - Fi : tap or click the Wi - Fi image .
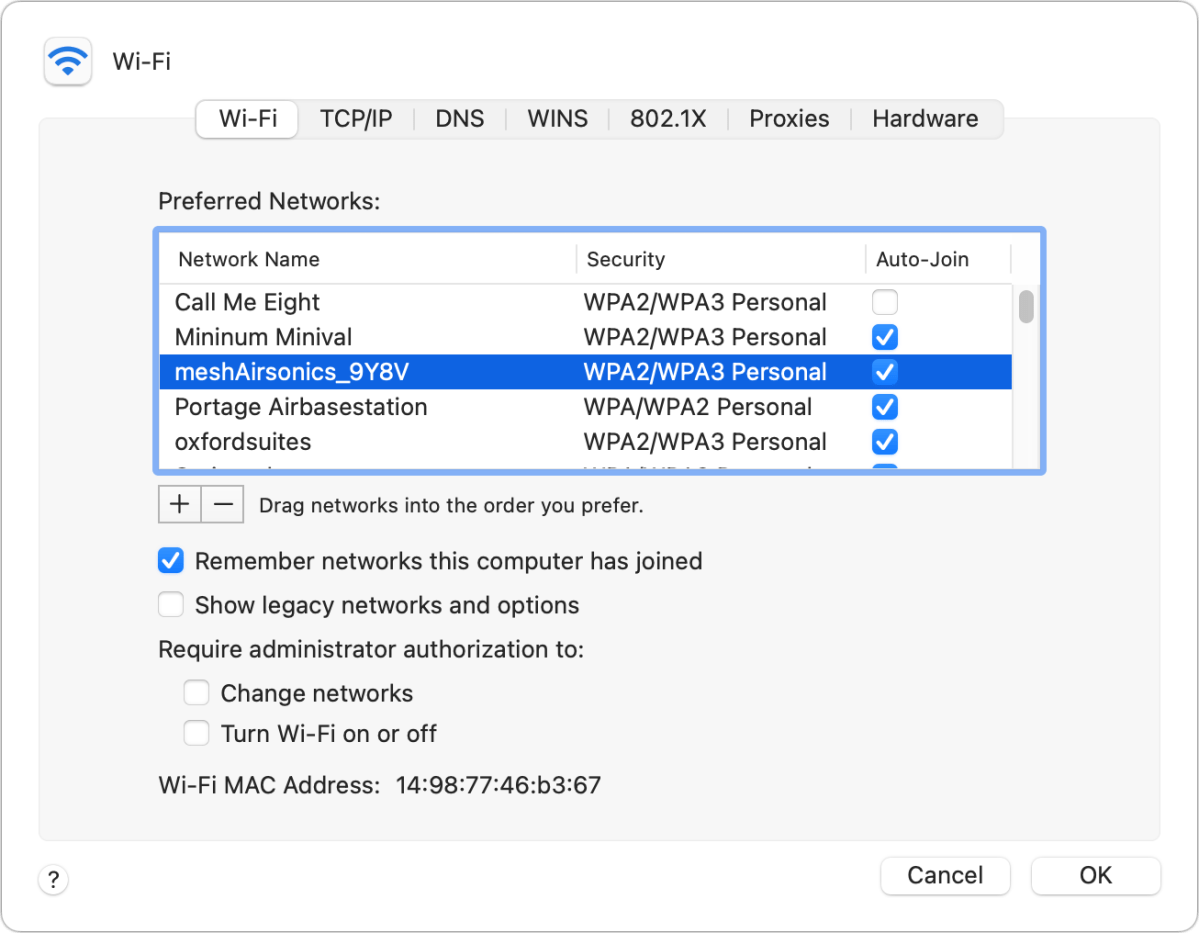
Or you could “ block ” the Wi - Fi web from your stored options , which disconnects your twist and wo n’t mechanically reconnect to the same web :
This Mac 911 article is in reaction to a question submitted by Macworld reader David .
Ask Mac 911
We ’ve compiled a list of the questions we get ask most frequently , along with solvent and links to column : read our top-notch FAQ to see if your enquiry is covered . If not , we ’re always front for young trouble to solve ! Email yours tomac911@macworld.com , let in blind seizure as appropriate and whether you want your full name used . Not every interrogation will be resolve , we do n’t reply to electronic mail , and we can not provide direct troubleshooting advice .