It can be nearly the worst sensation to have – a creeping dread that an unknown somebody has entered the elbow room you ’re in , who you ca n’t see . When you wrick around , there ’s nobody there . But it ’s even worse when you change by reversal around and there is someone there . This can happen with your on-line life-time when you have an account hijack , potentially silently , and political party have sex or unknown to you are despoil through your data point or monitor you .
An Apple ID is no exception . But you could track both chief threats ( other twist and logins ) and secondary ones ( apps and other service ) sharing accession . You should check which devices and sound numbers game are consort with your Apple ID and then do a universal audit with Safety Check , put in in September 2022 .
Check for unwanted devices
To view a inclination of gimmick that Apple considers logged in and confide for your Apple ID history , do one of the following :
If you see a equipment you do n’t recognize :
This twist is no longer considered a trusted gimmick for the purposes of access to your Apple ID account and can no longer access new information sync via iCloud servicing . However , it may hold any information that was downloaded or hoard locally .
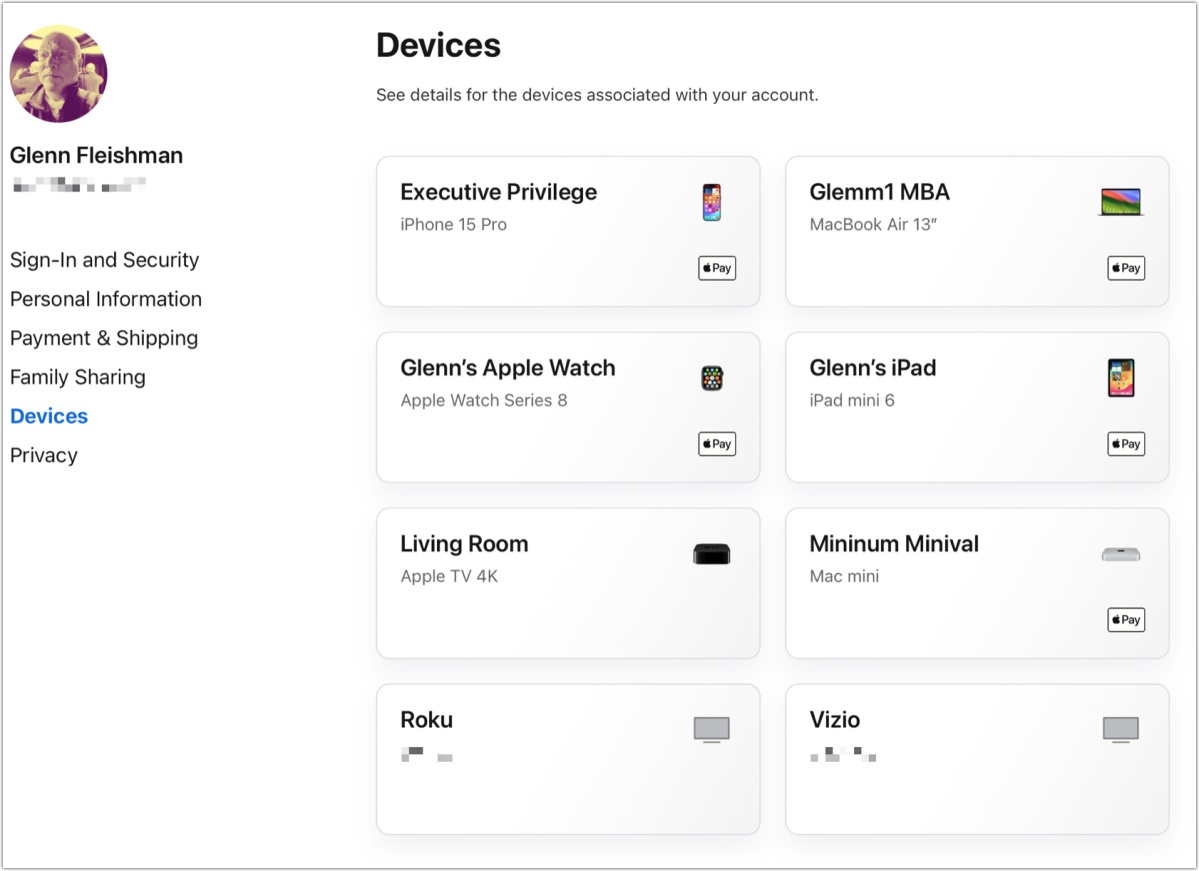
Check that you recognize every device logged into your Apple ID account.
arrest that you recognize every twist log into your Apple ID account .
Foundry
Check for unwanted phone numbers
Apple relies on sound numbers you add during setup or change later to give you extra way to verify account access if you ca n’t get to a desire machine or have other account issues . you could check on these trust number ; if you do n’t recognize a headphone number , make cover capture or take photos and make a note . In each of the above places , you could remove an unwanted number .
Here ’s how to find the numbers and remove them :
Trusted phone numbers can verify a enter to your chronicle — dangerous when you do n’t recognize the issue .
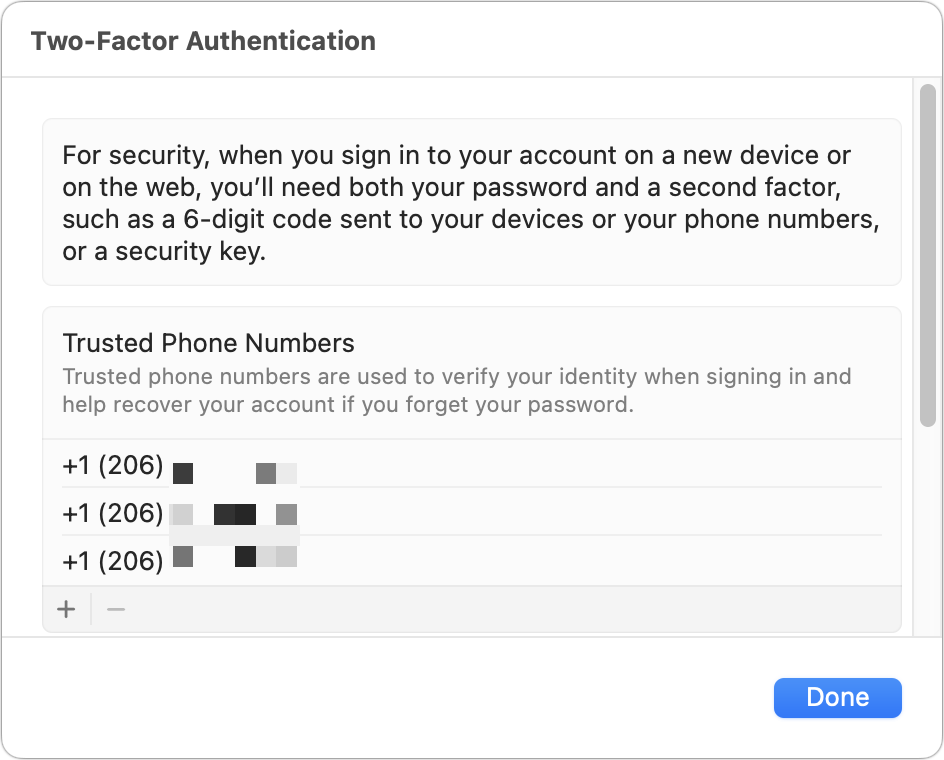
Trusted phone numbers can verify a log in to your account—dangerous when you don’t recognize the number.
Perform a Safety Check
initiate in iOS 16 , you’re able to use a new secrecy and safety feature film called Safety Check . It ’s design to assist people who are victims of stalk , intimate partner wildness , and similar situation ascertain whether they are being monitored by or connected to anyone they do n’t want to be , and remedy that site . It also has extra base hit pathways built in , as well as advice on contact real - world resources for help .
Safety Check provides a fast and safety - keep way to see with whom you ’re sharing info or who has entree to your placement .
encounter the feature atSettings > Privacy & Security > Safety Check . Note that on every screen , there ’s a Quick Exit link . water faucet that , and it essentially force quit preferences instantly , both preventing someone from encounter what ’s on your screen and not re - opening a track back to Safety see if mount is relaunched .
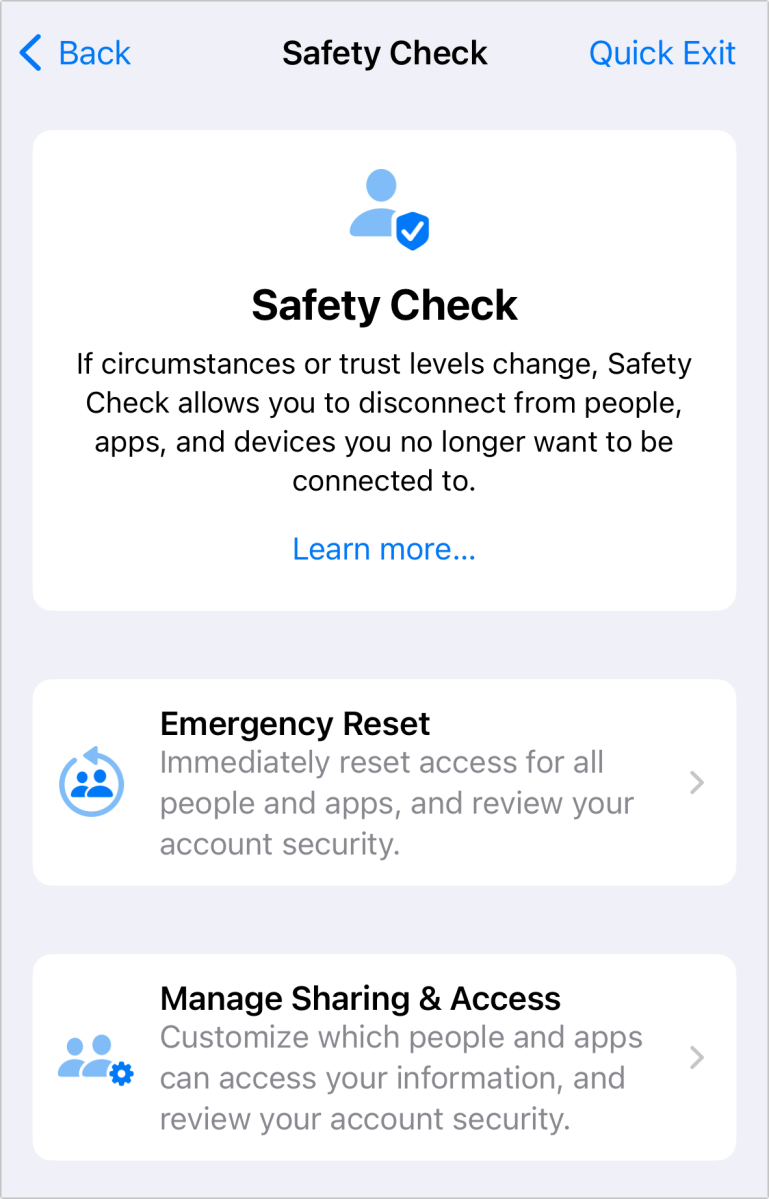
Safety Check provides a quick and safety-preserving way to see with whom you’re sharing information or who has access to your location.
Apple provides two nerve tract : Emergency Reset , which essentially trim back your iPhone and Apple ID account off from everything else and lets you readjust countersign ; and Manage Sharing & Access , which offers a review of options with options to convert and restrict at each step .
Apple offers an extensiveguide to this characteristic , worth confabulate in preparation for using it to verify you know what to expect for and the event of engaging any of its options .
This Mac 911 article is in answer to a question submit by an anonymous Macworld reader .
Ask Mac 911
We ’ve compiled a leaning of the interrogative sentence we get asked most ofttimes , along with answers and links to columns : read our super FAQ to see if your doubt is covered . If not , we ’re always looking for new problems to lick ! Email yours tomac911@macworld.com , including screenland captures as appropriate and whether you want your full name used . Not every doubt will be answered , we do n’t reply to email , and we can not put up unmediated troubleshooting advice .