The best arm against Mac malware is your mind : recognize the primal aspects of illegitimate software program , and configure your Mac aright , go a long way toward avoiding a takeover . We ’ve seen two new lesson of OS X malware in the last hebdomad — Backdoor . MAC.Eleanor and OSX / Keydnap , both of which are embarrass from fulfil unless a Mac ’s preferences are too big . The power to set a Mac to be vulnerable is about to commute for the better in macOS Sierra , too .
And , as I ’ve write about here before , the job with malware typically is n’t you , a lecturer of a pillar that plow security and privacy . Rather , it ’s the behavior of all the masses you sleep together who are n’t techies , but estimator user — sometimes very primitive ones , no matter whether they ’re 5 , 35 , or 95 years old .
Apple has a burden of education , as do software developer as a whole , because while malware is n’t a problem of their fashioning , it ’s something that affects their customers and may deter the great unwashed from buying third - party software whether in or out of the Mac App Store . ( I write a few months ago that developersneeded to switch entirely to https deliveryof website and charge downloads to abridge Isle of Man - in - the - middle computer software highjacking , for illustration . )
But each of you reading this column can also help educate those who turn to you for Mac advice on how to configure their Mac , how to debar executing malware , and how to be generally less credulous . Many masses desire whatever a website or downloaded software package enunciate , and that ’s a bigger jeopardy than OS exploits .
The power is within you
Some malware , there ’s nothing you could do to avoid . That ’s largely software that leverages vulnerabilities in the operating scheme to install without verification or by masquerading itself as something it ’s not . You have to bank on the quick find by researchers or the God Almighty of an operating scheme .
Apple has in its back pocketXProtect , a listing of “ signatures ” that identify malware and block it from action . XProtect is an unlabeled part of Gatekeeper , which throttle how apps and other components run in macOS . ( Integotracks these updates ; Apple does n’t release line severally . )
But attack software like the two from this last week require mass to overcome blocks put in their way for become septic .
Backdoor . MAC.Eleanor is a Trojan horse distributed under the name EasyDoc Converter . As my colleague Lucian Constantin remark , it ’s “ distributed as a file converter applications programme through reputable websites that offer Mac software , ” but in reality does nothing . I ’ve discourage before aboutdownloading software system from any land site but that of the developer , especially since many download sites now box software at bottom of installers that also establish adware or other unwanted apps .
The vector of statistical distribution for OSX / Keydnap is strange , but it arrives in the mannequin of a ZIP archive that has to be extracted , and then a file at bottom must be double - clicked to found .
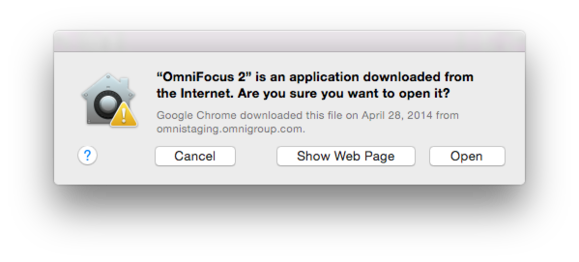
Neither app has been sign by a valid Apple developer certificate . Apple allow anyone to unite the developer platform , and apps can be sign by an combat-ready cryptographically secured certificate without getting Apple ’s approval , although that approval is required to make item uncommitted for purchase in the Mac App Store ( MAS ) .
Unsigned apps can only found in one of two ways : the first is by right on - clicking the app after it ’s download , selecting Open from the contextual menu , and then concord to plunge the app even though it ’s unsigned . This action only has to take position the first time it ’s launch , and it ’s retained from then on as a change in the app ’s attributes . The second is if the Security & Privacy system of rules preference pane ’s General lozenge hasAllow Apps Downloaded Fromset toAnywhere . In almost all cases , Mac App Store and describe Developersis the right setting .
This option worried developers and warhorse Mac users when it first appeared , as it seemed to herald a Clarence Shepard Day Jr. when the only selection would be a third one , which only launches apps from the MAS . That one is valid if you ’re administer a computer for someone else and want to prevent them from accidentally installing software outside the ecosystem for security or other reasons .
In macOS Sierra , the Gatekeeper option has been simplified : Anywherewas withdraw as a choice , and onlyMac App StoreorMac App Store and Identified Developersremains . However , unsigned apps can still be launched with the right - click sequence describe above . Requiring that in every illustration reduces the betting odds of someone setting the preference by accident . El Capitan bring up the stakes in a unlike way throughSystem Integrity Protection , which make it intimately impossible for software system to modify the content of many system file and folders , again reduce the chance for a small error to turn into a prodigious bungle .
Some confrere say in their particular disciplines or industry , many software developer create utilitarian utilities ( some are seldom updated , but they still work ) do n’t incommode to or lack the interest in going through Apple ’s signing system , and so they distribute their apps unsigned . While it ’s always hard to complain about hoi polloi generously distributing software , they ’re contributing to the overall risk by training user to open obscure software .
The takeaway lessons
Two while of Mac - focused malware in a week is a rare happening , and it may foretell nothing at all . While there are many felonious syndicates and independent developer create software to infiltrate computing machine , roving equipment , and electronic connection , the eminent legal community that Apple has set keeps it from being low - string up fruit for assaulter .
But it ’s also a star sign of something that I and many others have warned about for years . The Mac is n’t resistant ; it ’s just resistent . Its nonage percentage of the computer market place , couple with speedy upgrade by most owners to new edition of the operating system , have n’t made it profitable enough . That may have changed , and it may become more quotidian to see malware of the variety that requires our intimacy to install .
If you desire some advice to give others , here are the prominent takeaway :