AirDrop became very popular in China lately , for the unproblematic reason that the function completely disguises the transmitter ’s contact details . As AirDrop transmission does not take position via the internet or cellular headphone meshing , but from iPhone to iPhone via Bluetooth identification and a local Wi - Fi connection , it ’s extremely hard , if not out of the question , for authorities to name transmitter . This allowed protesters to change of import content , meme , and photograph with each other without the police being capable to collapse the networks .
With the launch of Io 16.1.1 around a twelvemonth ago , however , Apple put in place atime limit of 10 minuteswhen divvy up connections with Everyone , rather than the default option Contacts Only gear up . The prescribed pedigree was that this move was intended to combat AirDrop junk e-mail and maltreatment , but the suspicion was that Apple was acceding to the wishes of the Chinese government – particularly as the change applied first in China .
Now a Chinese province - licensed security system company from Beijingclaims(viaBloomberg ) it has successfully cracked the system and obtained the contact details of an AirDrop sender . The firm says its experts have found log information for the AirDrop process on a recipient ’s iPhone ; the gadget name of the transmitter ’s iPhone , along with their email and phone bit , is saved on the target iPhone during data transfer . Although the latter two details are converted into hash values , the security measure company has found a method acting to exchange these hasheesh values into readable school text .

Device details in the console logs.
We can affirm office of this title . We launched the console table on our Mac and AirDropped a filing cabinet to it from an iPhone , discovering from the console log data that the “ sharingd ” process is responsible for AirDrop . This check a dedicated sub - outgrowth call in “ AirDrop , ” but several other zep - processes were also active during the data file transference . We found the name of our iPhone in one of the pigboat - mental process , along with the specialty of the Bluetooth sign .
equipment details in the console table logarithm .
Halyna Kubiv
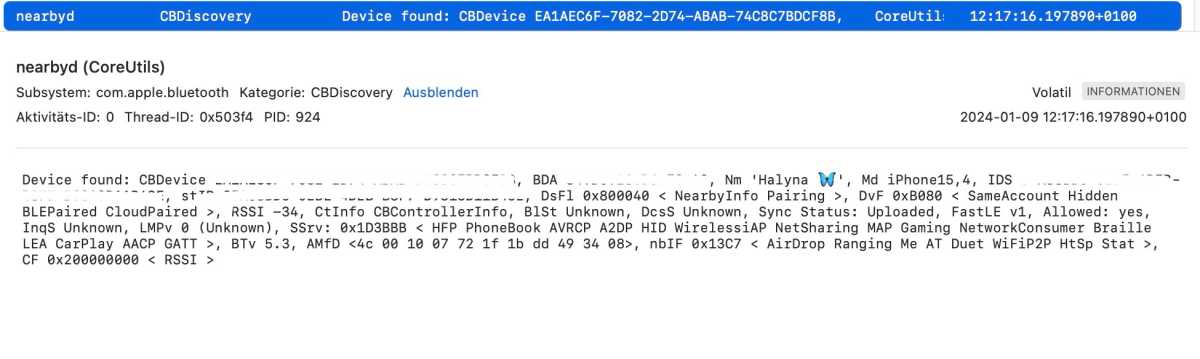
Device details in the console logs.
The “ AirDrop ” sub - process really salt away the hash values for the email and earphone phone number go to the contacted iPhone ( see screenshot ) , but we were ineffective to get at the plain text .
Console log during the AirDrop transfer
Last but not least , it should be noted that our Mac and our iPhone are trusted gadget , otherwise the AirDrop transfer would not work at all . Even with obscure contacts , the recipient must first authorize the data point transfer ; no extraneous files are transfer without their knowledge . If the reports are true , AirDrop is a threat to dissidents in dictatorial state , as they believe they can persist anonymous when exchanging files .
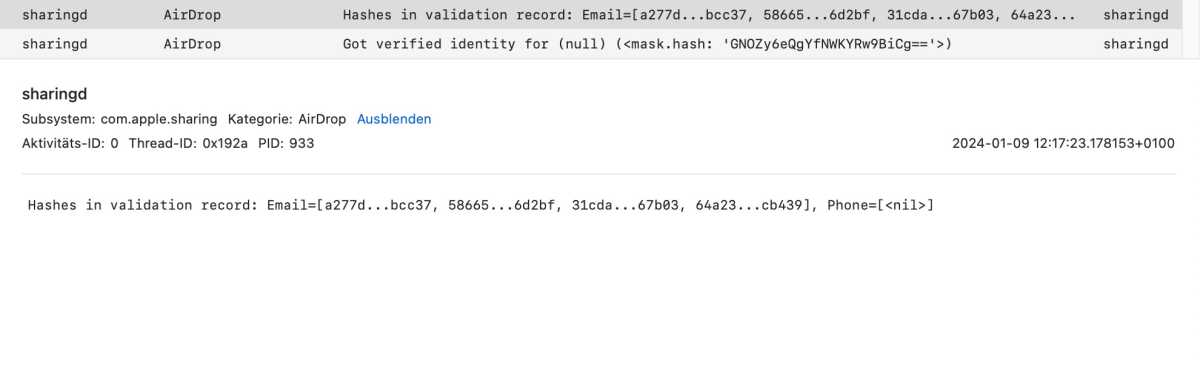
Console logs during the AirDrop transfer.
Why didn’t Apple fix the flaw?
security measure researchers have been warning Apple since at least 2019 that the AirDrop communications protocol is flawed and can be cracked . In August 2021 , the mathematical group led by Alexander Heinrich at TU Darmstadt presented a much more secure alternativecalled Private Drop .
The problem with AirDrop is that the protocol request the address and phone number control via the Apple ID from the transmitter ’s machine and the receiver ’s machine when establishing a connection if these are not in the destination Holy Scripture of both parties . Although they are stored as hash values , they are fairly light to decipher : the telephone set number consist only of fingerbreadth and is well-situated to decipher using a brute - violence attack . For emails , assailant suppose the usual alias structures , then look for possible matches in dictionary and database of leaked email .
According to Heinrich , it was only a matter of fourth dimension before the security gap in AirDrop were abused . However , the researchers have so far only intercepted the information during transmission endeavor . The fact that the personal data of AirDrop contact is stored topically on the iPhone was antecedently unknown .
Heinrich order Apple reportedly contacted the researchers from Darmstadt about the loophole way back when iOS 16 was still in maturation . However , Heinrich was unable to find out any important changes to the conveyance communications protocol security . Apple ’s difficulty would be that the newer and more secure interlingual rendition of the AirDrop communications protocol would not be rearwards compatible with old iOS version , he added .
This article originally appeared on Macwelt and was translated and edited by David Price .
This clause in the beginning appeared on our baby publicationMacweltand was translated and localized from German .