Topics
recent
AI
Amazon
Image Credits:Peter Dazeley / Getty Images
Apps
Biotech & Health
Climate

Image Credits:Peter Dazeley / Getty Images
Cloud Computing
Commerce
Crypto
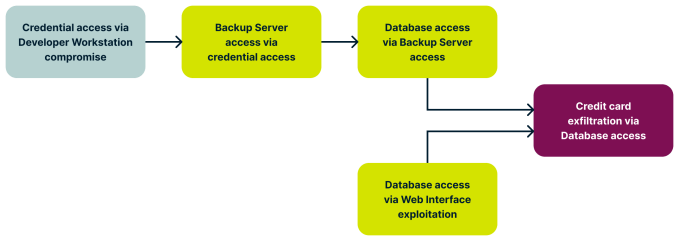
Image Credits:ExpressVPN
endeavor
EVs
Fintech
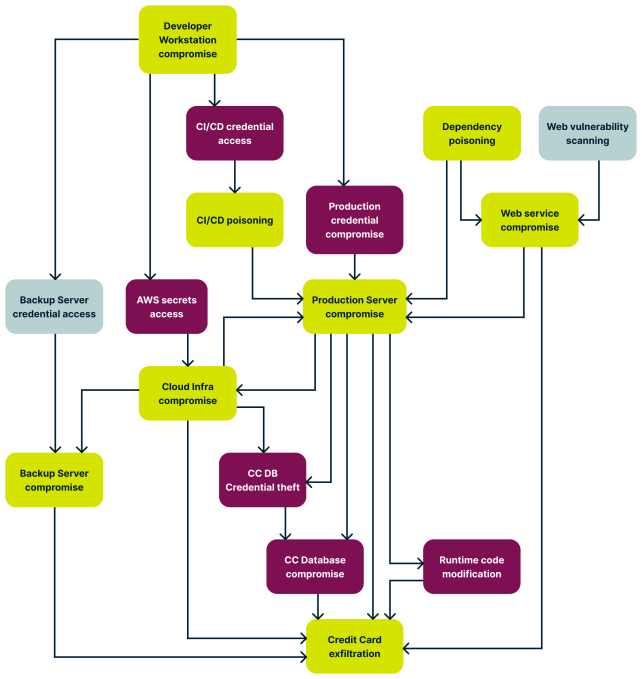
Image Credits:ExpressVPN
fundraise
gismo
Gaming

Image Credits:ExpressVPN
Government & Policy
Hardware
Layoffs
Media & Entertainment
Meta
Microsoft
Privacy
Robotics
Security
societal
Space
startup
TikTok
Transportation
Venture
More from TechCrunch
Events
Startup Battlefield
StrictlyVC
Podcasts
Videos
Partner Content
TechCrunch Brand Studio
Crunchboard
reach Us
In today ’s interlink reality , cyberthreats are everywhere , and they ’re always changing . startup ca n’t afford to snub the grandness of securing their digital base . Waiting until a surety breach happens can lead to severe consequence , such as financial loss and reputational damage .
Recently , ExpressVPN collaborate with Linking Help , the NGO behind UA.SUPPORT that provides pro bono effectual supporting to Ukrainian refugees , to carry on a terror modeling depth psychology . The target was to identify security business organisation and provide effective mitigation measure . Inspired by this experience , I want to share our methodological analysis with the wider community of interests and empower you to heighten your surety position — even with circumscribed resources and other concern pressures .
Unmasking exploits with threat modeling
Threat modeling is a fundamental practice for strengthening digital defence . but put , it involves understanding and knowing your organisation , so others ca n’t cause you harm . The goal is to raise awareness of security crack and understate the risk of potential effort by consistently analyze likely avenues for abuse .
Various terror modeling standard and framework exist , and the right choice for you depend on your specific context of use . Instead of telling you which of these to use , we will focus on the underlying methodological analysis that we used to conduct threat modeling for UA.SUPPORT , thereby generating efficient and hardheaded security good word .
Actionable security strategies for startup resilience
1. Know thy enemy
Identifying potential opponent and their objective is crucial for assessing why and how you may be aim . For instance , cybercriminals often target system that handle credit entry cards or personal identifiable information ( PII ) , while nation - body politic opposer may be interested in information for espionage or intelligence purposes .
In the case of UA.SUPPORT , potential opposer include :
○ Gathering intelligence activity on individual from Ukraine .
Join us at TechCrunch Sessions: AI
Exhibit at TechCrunch Sessions: AI
○ Compromising systems to advance wildcat access code , pull together sore selective information , or conduct espionage activities .
○ Disrupting the organization ’s program to hinder its ability to aid vulnerable person .
○ Exploit the PII of refugees for pecuniary gain .
○ Engage in wildcat cryptocurrency mining or set up ransomware onrush
○ Utilize the establishment ’s base to distribute malware to unsuspecting users .
Once we identify who the potential adversaries are , we can reckon at what they perceive as “ crown jewels . ” We can then use this to embark on breaking downwhythey might place you , andhowthey would go about doing it .
2. Know thyself
To figure out how threats might attest themselves within your environment , you must first gain a clear apprehension of your environment .
The just agency to achieve this is by engaging with the nonmigratory expert who developed or negociate the systems , components , and processes you use . Their expertise can provide valuable insights into the privileged workings of system as well as the flow and interchange of data . This operation helps create an stock list and design that captures the intricate web of business and technological interaction at dramatic play .
In our engagement , key areas we reviewed include :
Examining these provide insights into likely vulnerability that adversaries could exploit .
3. Anticipate weak points
resister have various method to gain approach to systems , and by word detailed , hypothesis - driven inquiry , we can pinpoint potential unaccented points that opponent may overwork .
In the suit of UA.SUPPORT , it is crucial to analyse the direct fundamental interaction between refugees and effectual volunteers . This analytic thinking involves focusing on the following area :
By expanding our examination and going into coarse-grained specifics , we gain a deeper reason of how antagonist might navigate each organization in their pursuit of via media .
4. Step into the adversary’s shoes
To efficaciously handle potential exposure , see the paths of least resistance that resister may overwork . startup like you have an reward in this heed , as you are probable to possess intimate cognition of your systems because of your sizing . This knowledge enable you to deal an in - astuteness analysis of potential risks and weaknesses .
For example , if the vexation is client credit card theft , startup can ask specific questions during threat modeling . Some of these question may include :
visualise potential attack scenarios using tools like an attack Sir Herbert Beerbohm Tree diagram can also be helpful . This glide slope allows you to represent out the progression an resister might make from one compromise point to another in quest of their end destination . For instance , compromising a developer ’s workstation could provide access to secrets and credentials , which could then be used to point the CI / certificate of deposit line , cloud infrastructure , product system , or even backup systems . Subsequently , the attacker could swivel from a compromised backup waiter to the associated database , ultimately advance access to coveted reference card selective information .
The attack tree diagram for such an attack may look something like this :
Of naturally , real - humanity system are more complex than that , and you may end up with an onset tree that may have multiple outgrowth and level :
By understanding the system landscape painting and obtaining answers to these inquiry , you could picture how attackers might chain actions to progress toward their objectives .
5. Put an evilness score on it
To prioritize effort to address security risks , apply a marking system to assign threat wads . This allows for a fast evaluation of how critical each stone’s throw is in a potential plan of attack . Several parameter can be consider when specify these scores :
By summing up the scores for each whole tone , you’re able to better understand the potential risk you look , and prioritise mitigation efforts based on the high - scoring threats . This approach ensures that resource are allocated to the most critical areas first .
After add together up these scores , this sampling musical scale can be used to evaluate overall risk :
Implement proactive security measures
Once likely vulnerabilities and high - priority threat are identify , take proactive steps to address them . This include implementing security measure controls and countermeasure to extenuate the identified risks .
Accept, mitigate, or transfer
Based on the scourge scores , limit whether to live with the risks , mitigate them by apply additional safeguards , or transport them by leveraging third - party vendor or solutions .
Common proactive security measure let in :
Update scores
As you put through security auspices , it is important to refresh your threat scores accordingly . This will help oneself you reassess the effectualness of your newly implement security protection by reflecting the likelihood of threats occurring .
Continuously monitor and adapt
Threat modeling and proactive security measures are not one - fourth dimension activities . You should regularly look back and refresh your terror models as the business organisation and threat landscape painting evolves . Additionally , it ’s essential to foster a culture of security department awareness and answerableness throughout the administration by encouraging employee and volunteers to promptly account any surety concerns or incidents .
The value of proactive cybersecurity strategies
Cybersecurity is a complex and multifaceted field , and even with thorough threat modeling , there ’s always a risk of via media . Nevertheless , each proactive step we take to procure our organisation makes it more unmanageable for adversaries to compromise us .
The finish is n’t needs to be the debauched sprinter . Instead , our focus is on outrunning others being targeted and stay one stone’s throw ahead . By investing time and effort into proactive cybersecurity strategies , we elevate our overall security strength , increase our chances of staying forrader and protecting our digital assets efficaciously .